Cybersecurity is a priority for companies and governments. New regulations and industrial requirements have reinforced the need for independent third-party organizations that can help manage the cyber risk of systems, assets, and products/ services. Today, a very large majority of IoT devices are vulnerable to cyber-attacks. Manufacturers should make sure that they implement these minimum “security by design” requirements for their new products.
1. Today’s Status of Cybersecurity covers IoT Devices
Today, a very large majority of IoT devices, for example, smart building elements, vehicles connected to smart transport infrastructure, or gadgets that can be controlled remotely through mobile applications and the cloud are vulnerable to cyber-attacks. A recent report (Gartner, 2020) expected that 5.8 billion IoT endpoints will be in use by the end of 2020, only in automotive and enterprise environments. The market of consumer IoT products is projected to reach 153.8 Billion $ by 2026 (Verified Market Research, 2020).
With the increase in connected products volume and functionality, the cybersecurity risks associated with these products increased simultaneously. Mainly due to the volume of this market, as well as its connectivity to other high-risk environments, this becomes a serious issue. The combination of “smart” devices, mobile or web applications used to interact with them, and cloud services allowing them to connect with each other lead to the development of overlapped IoT ecosystems.
Based on this status of cybersecurity risk, the Open Web Application Security Project®, a non-profit foundation that works to improve software security, has identified Top Ten Web Application Security Risks (The OWASP Top 10).
The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications, also provides the reference for organizations to take their first step in adapting software that produces more secure code.
2. IoT Consumer Market – Conformity Guidelines & Certification Schemes
To cover the wide range of IoT consumer devices, several guidelines & certification schemes are now available defining the key security measures to implement within an IoT consumer device. They all define very similar “universal” requirements, where classes or profiles define the applicable requirement for a particular device
Below are some of the commonly used certification schemes to let consumers and organizations have clear picture on ascertaining the level of security assurance, including:
Bureau Veritas has defined 5 IoT security Levels to answer the market demand to provide consumers with cybersecurity levels that can be compared, address the current and impending regulations, such as the cybersecurity changes to the Radio Equipment Directive in Europe, lastly, to state compliance with existing guidelines
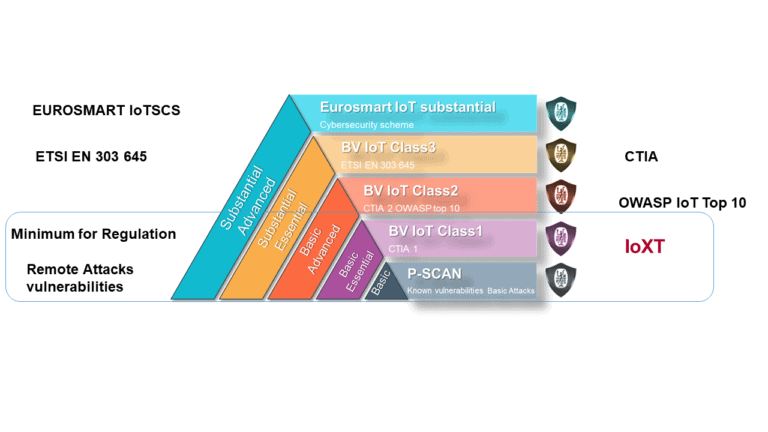
3. Minimum Requirements – Existing and Coming Regulations
Along with the awareness of cybersecurity over IoT devices in both consumer and enterprise markets, authorities from several regions are taking action to define concrete official standards, regulations, and even laws.
- GDPR applicable in Europe since May 2016, Cyber Security Act in Europe from 2019
- Inclusion of cybersecurity requirements in the RED directive expected in 2020
- Regulations in California & Oregon in force from January 2020
- NSCS UK code of conduit to be mandatory in 2020.
- Applicable Laws in Finland, Singapore & Japan
There is a minimum requirement of IoT Cybersecurity & Data Privacy Regulation:
- A secure configuration ready to use
- Private Data Management
- Vulnerability Management:
- Signed code & secure updates,
- Protection against exploitation of faults and known vulnerabilities
Manufacturers, retailers, and consumers are recommended to make sure they implement these minimum “security by design” requirements for their new products or the products they purchase.
Recommendations from Bureau Veritas:
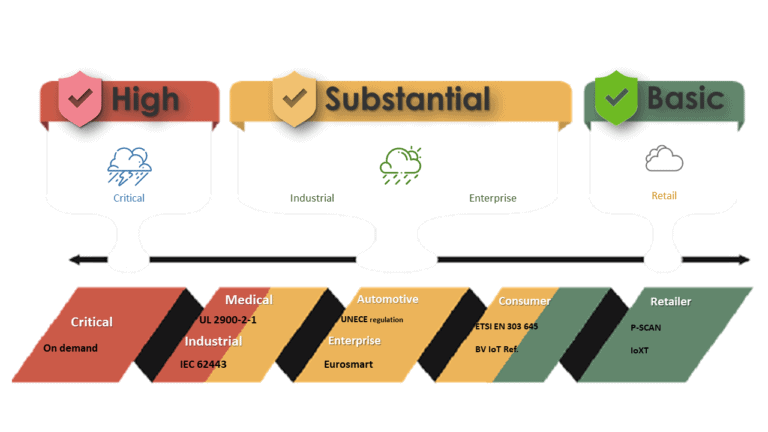
You may wonder how to ensure the products you manufactured, imported, or purchased are up-to-standard and proof from cyber-attack? The first step you can determine your IoT device is classified as which security level, and then gain the corresponding certificates with a professional third-party certification body.
For most consumer products, IoT devices are recommended to gain the IoXT certification since it is gaining momentum in the US, especially for Smart Home Markets. Any higher than substantial level is regarded as medical, industrial, military, or even national defense, which is not required for normal manufactures or retailers.
To protect your privacy and minimize the risk of being recalled on your products, take cybersecurity seriously today by gaining an authorized certificate.

Stephen LIM
Director, Business Development of Bureau Veritas Consumer Products Services
Content contributor: Bureau Veritas CPS HK (All rights reserved)
Bureau Veritas is part of the IoXT alliance, it is an authorized lab to deliver the above IoXT certification, as well as other global consumer and technology product testing, inspection/audit and certification. We offer one-stop-shop solutions to all your global market access needs. If you have any comments and/or questions about this article, please visit: https://www.cps.bureauveritas.com or click HERE for more technical webinars.





















